Can Ransomware affect the whole server network? How to overcome it?
- January 2, 2018
- 0
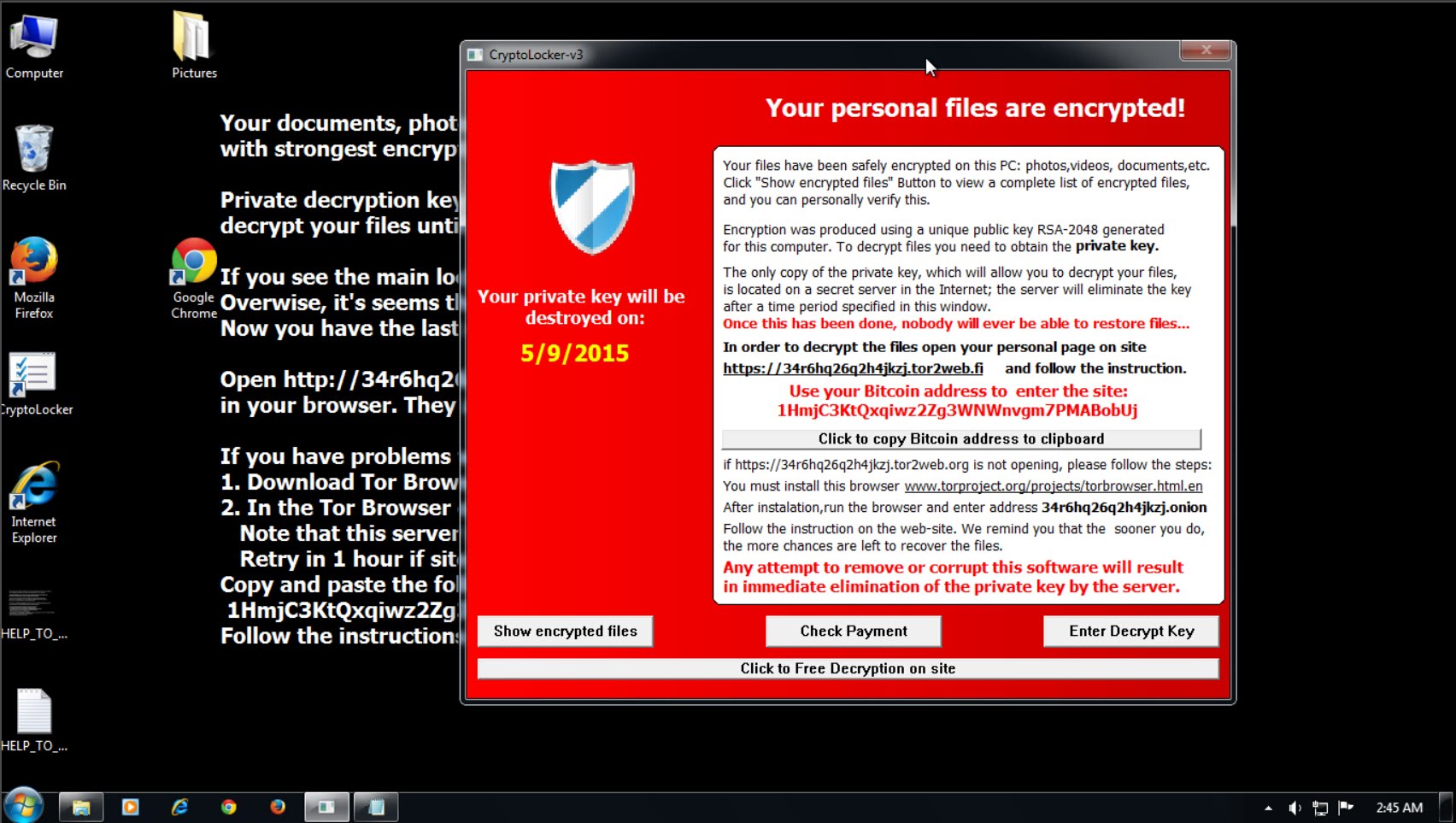
Ransomware is that kind of cyber attack that encrypts the important file(s) stored in a computer or a network of computers so that the person(s) cannot access the information unless a ransom is paid. This means that without a payment, accessing the file becomes impossible. Moreover, if someone even pays for it, there is no guarantee that there would ever be the chance of retrieval. Therefore, if such kinds of malicious activities are detected, it is most certain that the information has permanently been lost.
Most authors of Ransomware ask for the Bitcoin payment because it cannot help detecting the actual breachers in any manner. Previously, it was thought that it can corrupt only a single computer, but now it is proven that the whole network can get affected. It is possible for Ransomware to infect the Cloud and everything that is in there. If an individual’s personal computer is synchronized with the Cloud, everything gets locked.
How do cyber-criminals take control of an individual system?
It is a gradual process in which the criminals simply need to download a malware onto a device by letting the prey click (or download) on something by chance. Once the software gets downloaded in their PC, their computer gets invaded and all the files become encrypted one by one.
Phishing is the common trap to gain control over the victim. Think of an employee who has opened an email that apparently seems as if it were sent by his boss telling him to open some kind of file in the attachment. On an individual basis (who doesn’t work in any organization), it could be like fake bank related email in which he has to use/change his username and password using a link that was sent. The user reaches that link and enters the details that he is not supposed to share. The unauthentic third party can access his bank details as well as his personal computer that would soon be going to get invaded.
The most recent Ransomware attack
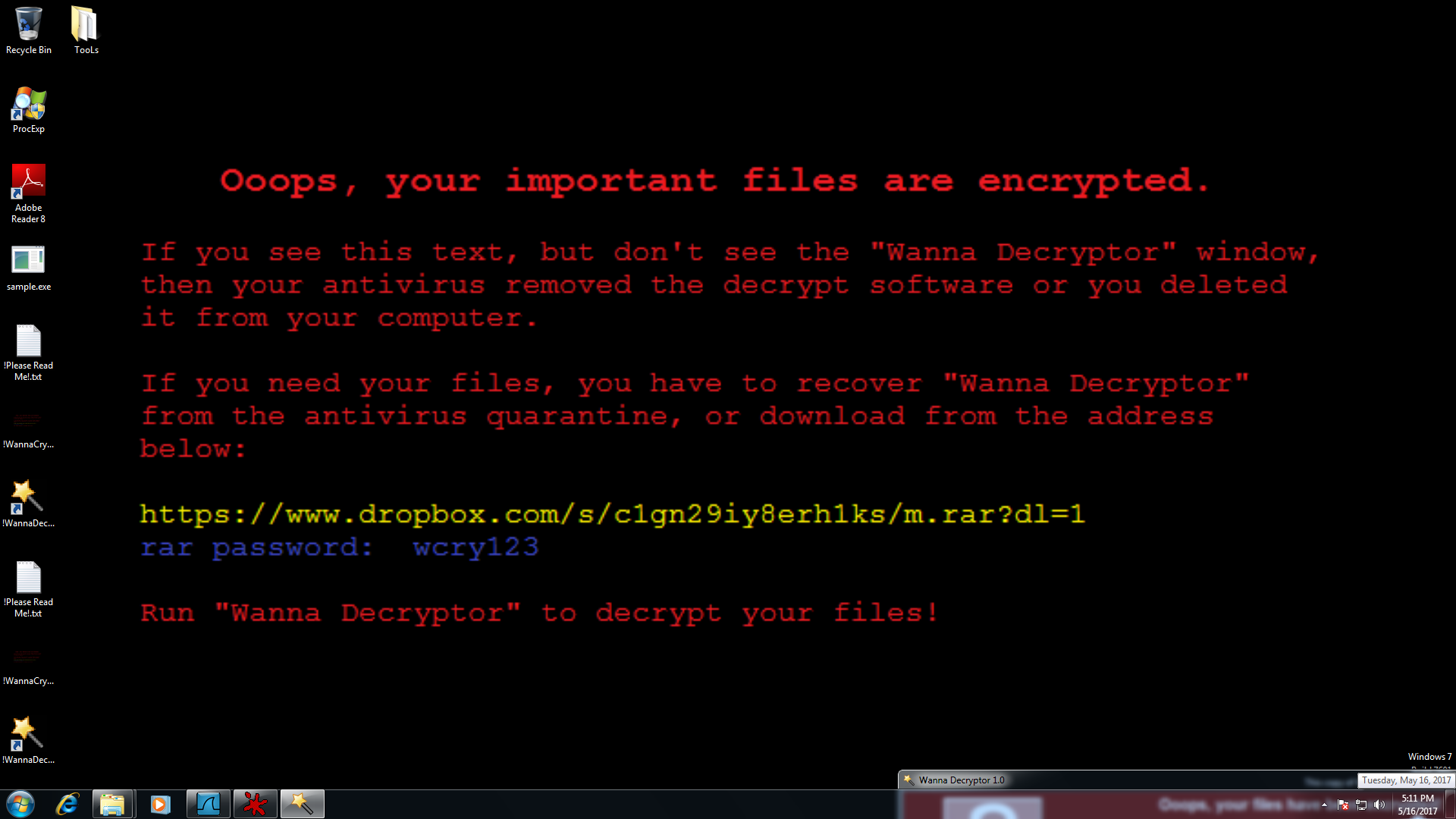
Wanna Decryptor (or WannaCry or wcry) is the latest Ransomware (mid 2017) that encrypted everything and showed only two files to the user. One file contained the program itself, and another one had step-by-step instructions on what to do next. These steps contained methods of payment through bitcoins. The warning is there to follow these procedures within a certain time limit, else the entire thing is permanently deleted. Although, there is still no guarantee that the payment would ever bring the files back to their original condition if given access at all. Moreover, the owner might forever lose them.
How to protect yourself from Ransomware?
Backup: There is no denying that having a backup of each file is a must and that too multiple times on different servers. Obviously, it is not just the hackers that are the only threats but also other kinds of hardware and software malfunctioning, accidents like catching fire, and so on. The Big Data has been growing over time and contains methods to maintain such a huge set of data.
Multi-layer security: It is possible that the threat penetrates single security layer. But if an organization takes more effective measures like multiple layer security such as Firewall then it would be least likely to get attacked. One isn’t sure how much determinant the hackers could be, nevertheless, it is the company’s duty to ensure the much-deserved privacy.
Also, make sure that the security suite is a reputed one that you are using who will likely take charge of everything and rectify if something happens. Go through the reviews online to get a general idea of the most trusted ones.
Update the software regularly: The hackers are aware of the software vulnerabilities if it is an old product. The software, therefore, needs to be updated, and that has to be installed by the end users on time if the new version is available. You may also enable the automatic updates so that you don’t have to remember when was the last time the updates were made.
Show the extension of hidden files: The default behavior of the Windows is to hide the extension of the files. Hence, make a practice of viewing the extensions and pay attention to “.PDF.EXE”, which should be regarded as suspicious because this is how Cryptolocker (another popular Ransomware) appears.
Disconnect from network: If you notice any kind of unfair activity and immediately remove the plug from the WiFi or any other source that is providing your PC the internet connection, you most probably would be able to disconnect the function of hacking in between and wouldn’t let it continue. This is a real-time scenario.
Challenges faced while dealing with Ransomware
Think about the scenario in which the file you had gets encrypted and its backup does not contain the latest information. This signifies that, although it is crucial to have the backup files in a completely separate storage unit, the backup files also need to be updated with time. This will help with reducing the chances of data redundancy.
The information on a large scale may reach in terabytes and that is not feasible to have a backup of literally everything. This is because it obviously consumes huge space and the requirement of related hardware and software infrastructure. Unless the details are not that much important and vulnerable to get exposed, taking backup should be limited to only certain kinds of data.
Secondly, the other server that holds the backup data, if not synced with the original, would require lots of time to get updated; if synchronization is done it would make it vulnerable as well just like its source server and other connected computer systems to be hacked!
One may come up with a solution of having varying servers that should be containing proper division or structures so as to make them easy to access and distinguish. The vulnerable and the most useful could be saved in a separate section, specific kinds that are important but less vulnerable could be stored elsewhere, and so on.