What is DMZ network architecture?
- May 15, 2019
- 0
What is DMZ network?
This term is coined from a geographic buffer zone that was installed between North Korea and South Korea at the end of the Korean War.
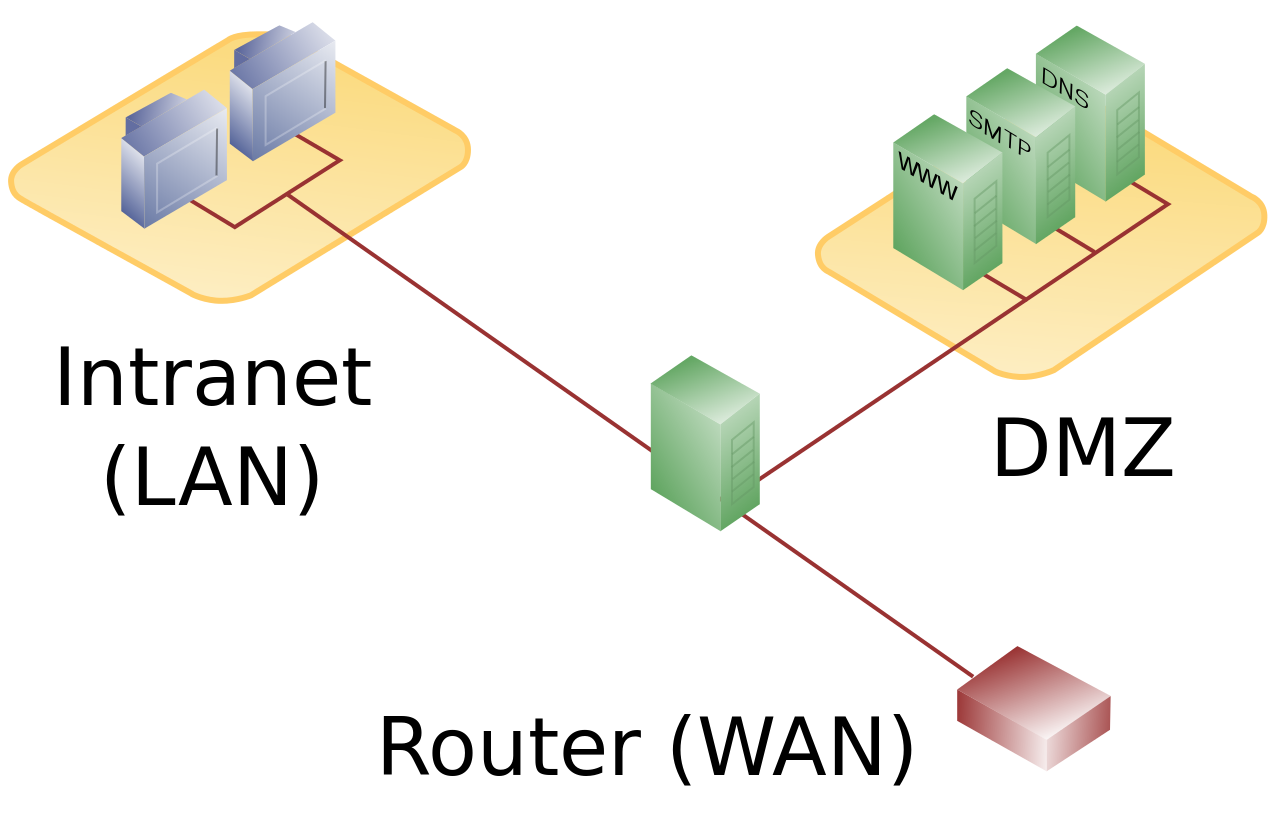
In networking, DMZ (demilitarized zone) is a logical or physical sub-network that holds most of a network’s externally combined services which attach to the Internet. Its principal goal is to give another layer of protection for a local area network (LAN).
Any network service that works as a server requiring an interface to an external network or the Internet can be fixed in the DMZ. The most typical services placed in the DMZ constitute FTP servers, email servers, VoIP servers and Web Servers. The choice on what server(s) to set within the DMZ is based on the whole computer security policy of an establishment and resource analysis of the disadvantages to placement outside of the principal domain.
In machine networks, a DMZ also sometimes identified as a perimeter network or a selected sub-network. External-facing servers, resources and services are also placed in the demilitarized zone. So, they are obtainable from the Internet, but the rest of the internal LAN continues unreachable. This produces an extra layer of protection to the LAN as it reduces the capability of hackers to quickly reach internal servers and data via the Web.
Whatever service granted to users on the public internet should be located in the DMZ network. Some of the most typical of these services cover web servers and proxy servers, also a voice over IP (VoIP), servers for email, File Transfer Protocol (FTP) and domain name system (DNS).
The systems operating these services in the DMZ are accessible by hackers and cyber criminals from anywhere and need to be strengthened to endure repeated intervention.
The architecture of DMZ network
There are many methods to design a network with a DMZ. The two fundamental ways are to apply either one or two firewalls, although most of the current DMZs are designed with two firewalls. This basic strategy can be developed on to build elaborate architectures, depending on the network specifications.
One individual firewall with a minimum of three network interfaces can be used to form a network architecture comprising a DMZ. The external network is set by joining the public internet through ISP connection to the firewall on the first network interface, the inside arrangement is formed from the second network interface and the DMZ network itself is combined to the third network interface.
There are plenty of techniques to build a network that covers a DMZ. The two most generally deployed systems are the three-legged model (single firewall) and a network amidst dual firewalls. All of these primary architectural settings can be farther developed to form a complex network architecture depending on the business or organizational requirements.
Three Legged DMZ Model (Single Firewall)
The three-legged DMZ model uses a single firewall with at least three network interfaces to make the architecture that holds a DMZ.
In this arrangement, the outside network gets created or made from the Internet Service Provider to the network’s firewall on the first network interface. The network DMZ is created from the third network interface and the internal network is then taken from the second network interface.
In the three-legged model, the firewall becomes the single point of failure for the whole network. It is also important to be capable to manage all traffic bound for both the DMZ and the internal network.
When representing the network architecture in this model, the colour codes are normally done to interpret the network zones. Green is usually used to designate the DMZ, purple for the internal LAN, red for the Internet, and a different colour to designate any wireless network zones that are being sustained.
Dual Firewall DMZ Model
To form a more reliable network DMZ, two firewalls can be utilised to set up the architecture. The “Front-End” firewall is set up to enable traffic to pass to and fro the DMZ only. The “Back-End” firewall is then set up to cross traffic from the DMZ to the inside network.
The two firewall or dual firewall model is regarded to be safer than the three-legged DMZ option as there would have to be two firewalls that would have to be negotiated for the network to be endangered. Some companies even go as far as to employ firewalls provided by two different companies to make it less inclined for a hacker to use the same security vulnerability to reach the internal network.
How does DMZ network work?
Many sets of firewall practice for traffic connecting the DMZ and the internet, DMZ and the LAN, and the LAN and the internet strictly manage which ports and what kinds of traffic are allowed into the DMZ from the internet, thereby limiting connectivity to particular hosts in the internal network and limiting unrequested connections either to the internet or the internal LAN from the DMZ, etc.
The larger protected approach to building a DMZ network is the dual-firewall approach in that two firewalls are deployed with the DMZ network located between them. The first firewall, also named as the perimeter firewall, is configured to let external traffic reserved to the DMZ only. The second or internal firewall only permits traffic from the DMZ to the internal network. This is recognized as more protected since two devices would require to be negotiated before an intruder could enter the internal LAN.
As a DMZ portions a network, safety controls can be tuned particularly for every portion. For instance, a network interruption detection and blocking system located in a DMZ and implementing web services could be configured to prevent all traffic except HTTPS requests to TCP port 443.
How does DMZs work?
DMZs are meant to work as a kind of buffer zone between the public internet and the organizational network. Deploying the DMZ between two firewalls indicates that all inbound network packets are chosen using a firewall or other security appliance before they appear at the servers where the organization hosts in the DMZ. This should be sufficient to block the most unexpected threat leads.
If a prepared threat is capable to get through the first firewall, they must then achieve unapproved access to those services before they can do any harm, and those systems are expected to be strengthened against such attacks.
Lastly, assuming that a strong threat actor is strong to breach the external firewall and rule a system hosted in the DMZ, they must still collapse through the internal firewall before they can reach delicate enterprise resources. While even the best-secured DMZ architecture can be breached by a stubborn attacker, a DMZ under attack should set off alerts, giving security experts sufficient warning to avoid a full breach of their company.
Uses of DMZs
DMZ networks have been a significant part of business network security for as long as firewalls have been in practice, and mostly for comparable reasons firewalls are deployed to preserve delicate organizational systems and devices.
The main benefit of utilizing a DMZ network is to present access to inevitable internet services from the public internet in a protected way. DMZ networks can be applied to separate and retain possible target systems isolated from internal networks, also to decrease and manage access to the systems from outside of the organization.
While many delicate resources can be preserved by deploying them inside the organizational system boundary, as dependency on admittance to services through the public internet has evolved so it has the necessity for organizations to implement those services to users located outside their perimeters.
Using a DMZ which has remained as the answer for hosting corporate resources to make them accessible to approved users.
Lately, companies have opted to use virtual machines or containers to detach parts of the network or particular applications from the rest of the corporate context. A network DMZ isolates the public from internal networks and sensitive data. So it is an obvious choice for bigger organisations with delicate data.
If you want to improve server performance then ApacheBooster will prove to be extensively beneficial. This is because it works wonders for low performing servers and troubleshoots them in no time once installed.