Best security measures to protect Linux Servers
- April 30, 2018
- 0
Linux server is a frequently used alternative of a Linux Operating System. It is designed in a particular way that it can handle the ever-increasing needs of business-related applications like System administration, networking, Web services etc. Linux servers are popular and are widely chosen over other servers as they are more reliable, flexible, secure and stable compared to their competitors in the market. Some of the dominant Linux Server OS are CentOS, Ubuntu, Slackware, Debian etc. Although, this operating system is safe, but the administrator(s) has to find out the best security measures to protect Linux Servers so as to maintain its functioning.
Security measures to protect Linux Servers
No matter how efficiently an infrastructure is set up, it has to address the issue of security. Failing to cater to the security measures to protect the infrastructure can prove to be disastrous. Some of the basic security measures that can be considered before or while setting up the applications are mentioned below:
Firewalls: Firewalls are the most integral part of all server configurations. A firewall can be software or a hardware that determines what services are to be made available to the network. A firewall has the ability to block or deny access to any port other than the ones that should be available publicly. Typically a server has numerous services running as default. Services include three categories – public services, private services, and internal services. A firewall makes sure that the access to your software is strictly based on the above mentioned categories. This restriction on access can reduce the number of attacks aimed at your server. There are plenty of firewalls readily available for Linux Servers. It only takes up a few minutes to set it and can be done during the initial stages of a servers set up.
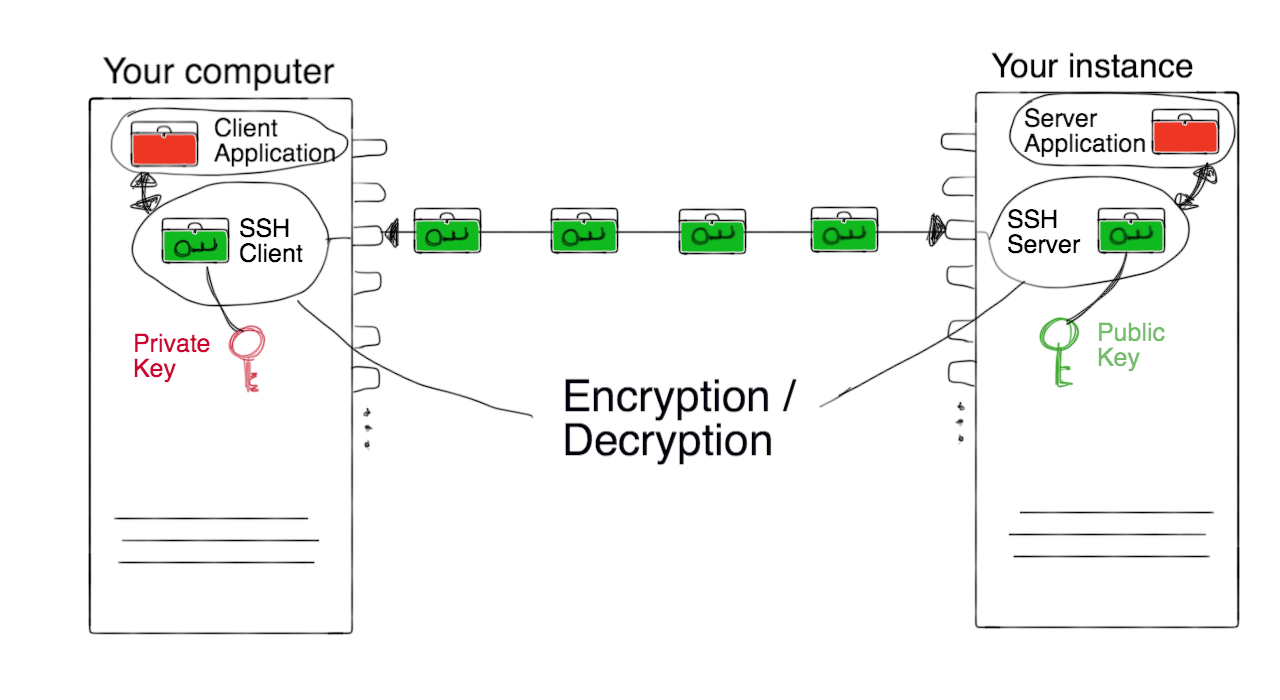
SSH Keys: It is a set of Cryptographic keys that are used to verify an SSH server as a replacement for password-based logins. Before authenticating a pair of public keys and private keys are made. The private key is usually kept hidden as a secret by the user, whereas a public key is shared with all involved. With SSH, all types of authentications are fully encrypted. SSH keys verification permits the disabling of password dependent logins. Since SSH keys have more data than a password, it becomes difficult for an attacker to come up with the possible combinations that the keys have.
Encrypt Network Transmissions: The need for encrypting all inbound data and outbound data is very crucial when it comes to the security of the servers. Use of tools like SSL/TLS can help in encrypting such data between the server and the client. This process will prevent anyone else from seeing the data transfer through the wire, thus keeping the server secure.
File Auditing and Detection systems for Intrusion: File auditing is done by comparing the existing system with a set of files or other characteristics of files, that are already in the system which is in a pretty good state. This process is done to identify the changes in the system that might have been verified. An Intrusion Detection System or IDS is a software that detects any unauthorized activity in the system or network. Majority of the IDS software that are host-based use the method of file auditing for checking if the system is altered.
Service Auditing: Service auditing is the method of finding the services that are currently running on the servers of your infrastructure. The operating system usually is configured to run a few services at boot as default. Sometimes, installing extra software can add in dependencies which are auto-started as well. Service auditing can be summed up as a method of knowing the services that are running on the system, the ports that are used for communications, also the protocols that are accepted. This information helps in configuring the firewall settings. Servers have many processes running to handle clients which can increase the security risks. This is where the service auditing comes into action. It helps in analyzing the type of network services that are running.
By default, Linux servers have an in-built security system in it. Hence, Linux servers are comparatively much more secure than the Windows even on the server, desktop or any other environment they are embedded. This security comes mainly because of its feature to be a multiuser OS. However, security measures to protect Linux servers are mandatory since Linux servers are not completely void of malware and viruses; nevertheless, it has pride in fixing the issues rapidly by its developers and users. This makes Linux one of the highly sought out servers in the world.